Introduction
Readers that are interested in the details of Circle’s unique security architecture, and how we have turned that into a REST API can contact us to request our technical white paper. This article is intended to provide a quick overview of the architecture, design and key components that make Circle work.
What is a Circle?
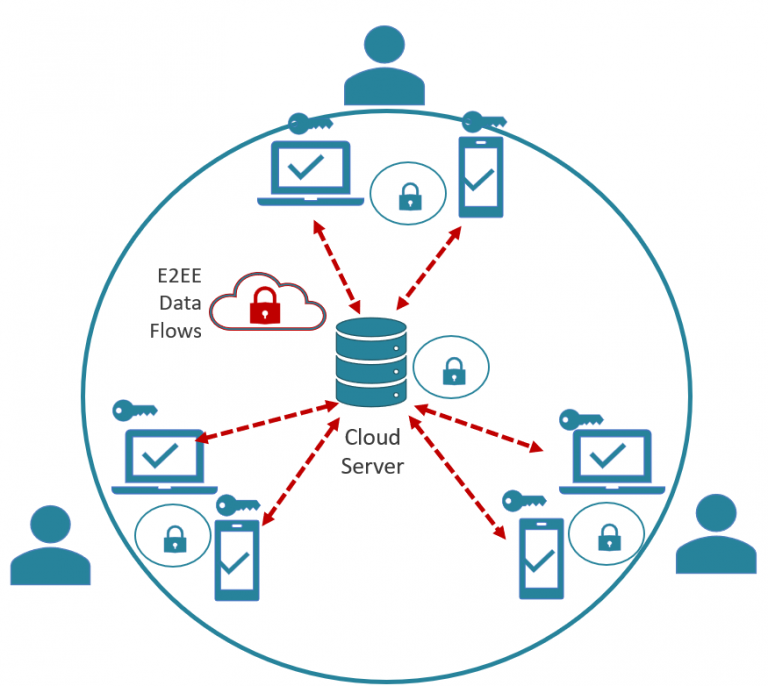
Invisible private network of devices
A Circle is a private network of unique devices tied to users who are invited and added by a Circle Owner. Every device that joins a Circle through a process of Peer Mediated Authentication, shares a unique AES 256 encryption key, which protects all of the data within it.
This includes user data and metadata used to communicate between devices in Circles. Thus, Circles are not only secure, they are totally private, with no visibility for outside actors into the contents, users or activities within them.
Key components of a Circle

Secure Capsules
Circle creates Secure Digital Capsules with unique encryption keys, that are only stored and accessible on the devices that are authenticated into a Circle.

Users
Users are not known to Circle as a system - the server or company - only devices. Users are anonymous, but devices can be linked together in a Profile. However, user profiles can be stored and shared inside of Circles, and with and between the Application Developer and Circles if desired.
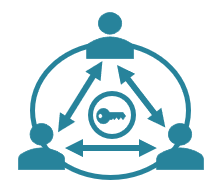
Distributed Multi-Factor Authentication
Circle Owners invite and verify the identity of Members personally via Circle’s patented distributed P2P multi-factor authentication process.

Circle Server
The Circle Server manages the invitation & authorization process, communication between devices, data transport, and data back-up, storage and restoration. It has no key for the Circles and Secure Capsules of data that is stores.

Keys Stored On Device, Not the Cloud
Only devices that have been invited and authorized to join a Circle have the keys to the Secure Digital Capsules it contains. The keys are stored on each user’s device – outside of their Circles of course. Currently they are protected in different ways. Where available, we use the device TPM to protect & bind them cryptographically to the device upon which they were authorized.
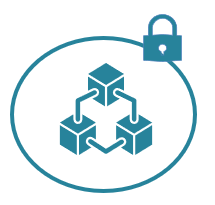
Internal Distributed Ledger
Circle has proprietary internal distributed ledger technology that can be leveraged to ensure data integrity, governance and provenance for enterprise and regulatory compliance. So, with Circle you can build functionality and applications that are BOTH private and secure AND compliant and trusted.
Circle Secure Capsules
Circle Secure Capsules can contain anything – files, databases, unstructured data. Your imagination is the only limit!
AES 256 encrypted containers for anything - files, databases, structure & unstructured data


Every Circle can create and contain an unlimited number of Secure Digital Capsules which are an information container or folder. In the API Methods, we call these Topics. Topics are groupings of information that you can share within a Circle. Topics can be public (the default) or private.
- Public Topics share the same encryption key as that of the Circle to which it belongs so all devices and members of a Circle have access to all the data in that Topic.
- Private Topics each have their own encryption key that is different from the encryption key of the Circle to which it belongs. As a result, a private Topic can contain data, messages, user identities, and metadata that are protected and shared only among a unique subgroup of the Circle.
A Topic can contain almost any data. You can use Topics to organize information-sharing rights to connect groups within a company, or to share specific information with specific teams
Circle Service
Circle Service powers the on-device functionalities of Circle's breakthrough Zero Trust, hybrid cloud + P2P security architecture

Circle Service
Lightweight Thin Client - install & forget
- AES 256 Encryption
- Key Management
- Invite + Authentication
- Circle Secure Capsules

Keys Bound to the Device
- Bound to device keychain / crypto wallet / Trusted Platform Module (TPM)
With Circle Service installed on their devices, end users get:
- Unrivaled data protection with device-based unbreakable AES 256 encryption and ZERO attack surface in the Cloud.
- Circle-of-Trust™ unspoofable Human-in-the-loop™ identity verification + authentication.
- Uncompromised privacy and data control - NOBODY but the data owner (whether that is the application developer or end user) can access their data - or metadata - EVER.
- Immutable data integrity and recovery with proprietary internal DLT.
Circle Web Services
Circle Web Services provide cloud always-on reliability and scalability without No Compromise on Circle's unique device-based security and privacy architecture
Circle Server
Circle Server supports the device-based Circle Service.
- P2P Invite + Authentication Service
- Secure exchange of AES 256 keys with PKI
- Data Store, Forward and Restore
- Data Transport Service Bus

Circle Server has copies – in data blobs – of each private secure capsule, but no keys. Zero ability to open them or even know what they are
Web hosting options

Developers can host and white label Circle Service on their servers for End Users to install.

Large developers can host data blobs & Web services on private cloud or on-prem if desired.
Circle Access Server
Circle Access Server manages user identity and authentication - with no access by Circle to either!
- Self-Authentication by User
- Encrypted User & Devices DB
- No unencrypted user PII
Circle License Server
Circle License Server manages licensing - and nothing else.
- Only knows customers and usage
- Has no access to Circle Server or Circle Access Sever.