Introduction
Circle Access provides developer and Enteprise customers with two different UX options that can be implemented in 3 ways:
Implementation Options
Circle Access provides developer and Enteprise customers with two different UX options that can be implemented in 3 ways:
- Circle Access Mobile - as a standalone authentication solution to log into any Web site or application.
- Your Smartphone is You.
- By scanning a QR code, the end user can log-in to any Web site or application on any device (mobile, desktop/laptop device, tablets, etc.)
- Circle Access Desktop - as a standalone authentication solution for Desktops only
- Your Device is Your Login.
- User must have Circle Access Desktop installed on the device that is logging in to the Web site or application directly.
- Currently only supported on Windows - MacOS users are given Circle Access Mobile as option.
- Circle Access Lite - where the user needs no device installation.
- Browser based configuration
Whichever you choose, all use Circle Access cryptographic, credential free authentication to protect access to your Web sites and applications.
Using Circle End-to-End Data Protection to Implement Credential-free Authentication
It is also possible to implement Credential-free Authentication with Circle Data End-to-End Data Protection by integrating with any Identity and Access Management systems - whether that is the back end of a Web site or application, or an integration partner of Circle such as Auth0, ForgeRock, Ping Identity and others. In this case, the role of Circle is restricted to protecting data used for authentication purposes in Secure Capsules that are controlled by the Web server / application or IAM platform. This is a very different approach which requires development expertise, resources and the functional capabilities of such systems. There are many benefits and capabilities of Circle Secure Capsules that go far beyond storing authentication data and can be leveraged in this implementation approach. If you are interested in this, we suggest that you contact us for a free consultation before starting.
What Is Circle Access Cryptographic, Credential Free Authentication?
With Circle Access, there are no credentials - i.e. a user name and password, or any other method of creating and storing 'secrets' on a server that is used to authenticate a user. All such methods are deeply vulnerable to attacks. Circle Access replaces with a radically better approach that achieves authentication with 3 very strong factors:
- Something You Have. A smartphone, PC or laptop.
- Something You Are. Biometric verification, with the option to escalate to Human-in-the-loop Identity Verification with Circle-of-Trust.
- Something You Do. Validation of a cryptographic authentication that can only be done with the private key uniquely created on and bound to the endpoint device controlled by that human end user.
You can learn more about that here.
While the Circle Access server does have a user concept, it only knows a User ID. All personally identifiable information (PII) - including emails and phone numbers - are stored only on the endpoint device, and only hashes of them are stored on the Circle Access server. There is no information on users that Circle Systems - or an outside or inside attacker - can gain access to on the Circle Access server.
User Experience Options
Users have different preferences, and use cases have different requirements. Circle Access provides two different authentication UX models to flex to whatever is best for your needs overall, or also enable you to offer this choice to individual end user.
Circle Access Mobile Application
The Circle Access Mobile Application is available and downloaded through either Google Play or Apple App Store. It is a secure mobile authentication app like no other.
- Your Phone is your universal log-in
- No install required on endpoint devices
- Continuous authentication
- Biometric identify verification
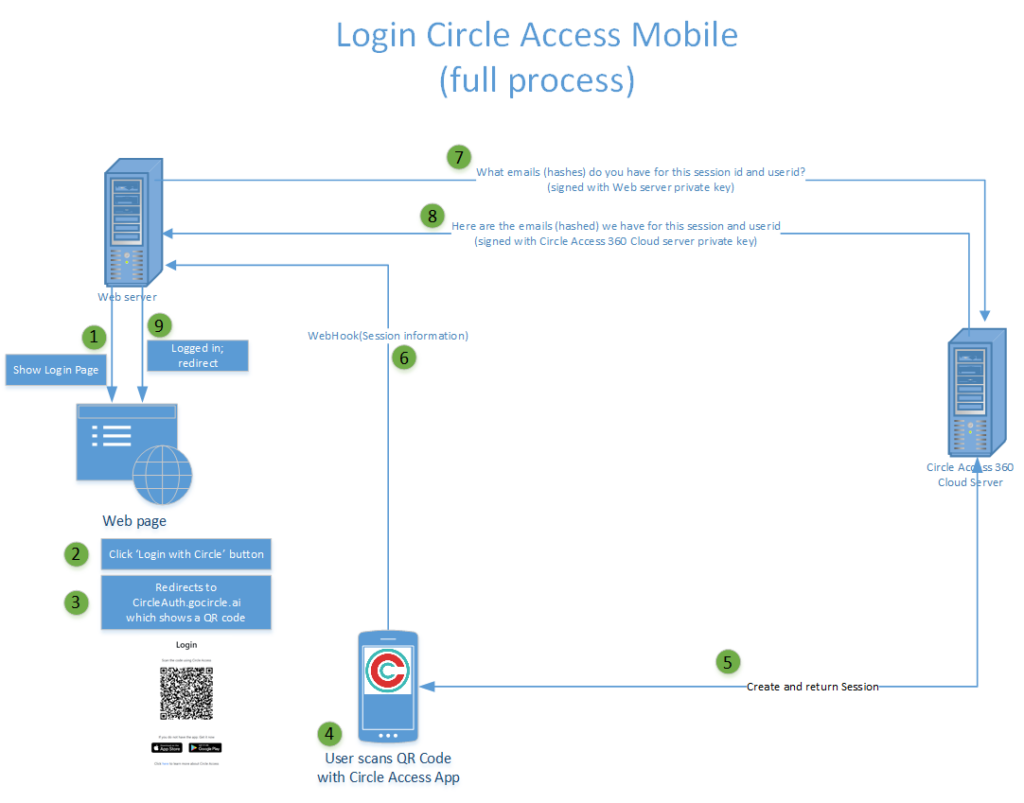
To log-in to any Web site or application, the user scans a QR code is presented by that Web site or application. The Circle Access Mobile can then communicate securely to that Web site or application:
- The User ID;
- Hashes of all the emails which that user has registered and authenticated with Circle Access.
The Web site can then look this up in its Identity & Access Management database (whether that is internal or through a platform partner) and - if there is a match - be sure that the device and end user on the device are authorized. The really nice thing about Circle Access Mobile is you can now use this to log-in to Web sites and applications on other devices - anywhere in the world - but with the unrivaled security of device-based, cryptographic authentication. And of course with absolutely no credentials to forget, lose or be stolen, or extra steps of traditional MFA to perform.
Circle Access Mobile Components
The Circle Access Mobile application is available on Android / Play Store or IOS / App Store. It has three major components all rolled into a mobile application.
- Circle API. Which runs all of the on-device key management, encryption and authentication functionalities which power Circle's unrivalled identity, data security and privacy capabilities.
- Circle Access API Libraries. Which securely manages all the on-device functionalities and calls to and from the Circle Access server and the Web site or application it is protecting.
- UX and application workflows. Which support UI and functionality for the end user features.
Since Circle Service is installed as part of Circle Access Mobile application on an endpoint device, all of Circle API's other capabilities are available to be leveraged by developers. If you are interested to explore this further, please contact us.
Circle Access Mobile Features
The Circle Access Mobile application incorporates all the features & functionalities required for an end user to:
- perform cryptographic, credential free scan & go authentication for any Web site or application to which it is integrated;
- add, authenticate and manage email addresses, recovery options and other needs;
- connect and authenticate with Circle Access Desktop when that is supported and offered by the Web site or application.
For details on these features, please see:
- Circle Access Mobile User Guide
Circle Access Desktop
Circle Access Desktop installs thin agent on your endpoint device which has the following characteristics.
- Install 1x & forget - runs as a Service.
- Your device is your auto log-in
- Sync multiple devices
- Securely creates and stores unique, private encryption keys for the purposes of:
- cryptographic authentication;
- secure, private client-side storage of data (Secure Capsules)
Circle Access Desktop Components
Since Circle Service is installed as part of Circle Access Desktop on an endpoint device, all of Circle API's other capabilities are available to be leveraged by developers. If you are interested to explore this further, please contact us.
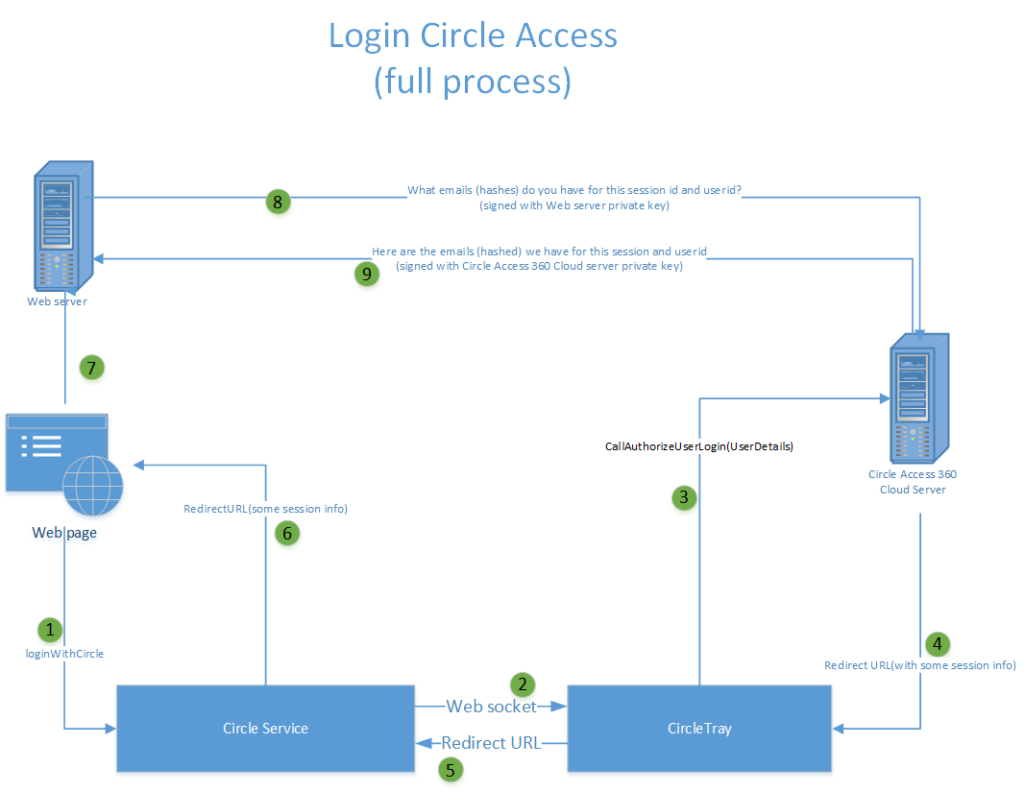
Circle Access Desktop is a thin agent that, once installed, runs and shows up in the Windows System Tray. It has two major components:
- Circle Service. Which runs all of the on-device key management, encryption and authentication functionalities which power Circle's unrivalled identity, data security and privacy capabilities.
- Circle Tray. Which supports UI and functionality for the end user features. Circle Tray includes the Circle Access API Libraries, which securely manages all the on-device functionalities and calls to and from the Circle Access server and the Web site or application it is protecting.
Since Circle Service is installed as part of Circle Access Desktop on an endpoint device, all of Circle API's other capabilities are available to be leveraged by developers. If you are interested in exploring this further, please contact us.
Note on MacOs Support
- Circle Access Desktop - which includes Circle Service, integration with Circle Access Mobile, and the end user features below - is not currently supported on MacOS. We will release this during Q3, 2022.
- Circle Service - the thin agent software itself that works together with other APIs in Circle Guard, Circle Vault and Circle Prive - is supported on MacOS.
Circle Access Desktop Features
A simple UI is available for users to manage key features. For details on these features, please see:
- Circle Access Desktop User Guide
Implementation Options
As noted previously, Circle Access provides developer and Enterprise customers with two different UX options that can be implemented in 3 ways, leveraging the Circle Access API and Cloud Server to enable a nearly code-free implementation. As with any authentication solution, the Web site or application owner must implement the UI that enable the end user to use whichever option they have selected.
Whichever implementation option you select, Circle Access works the same way. When an end user arrives at your Web site or application requesting authentication, it really only has two questions that needs to be answered:
- Do I have an account for this users?
- Is this the actual user that is authorized to access that account?
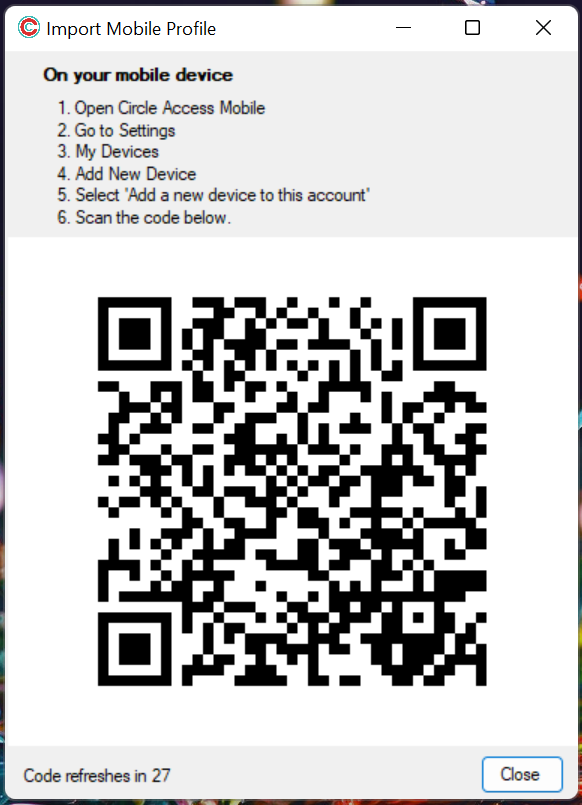
Circle Access answers both of those questions with one simple call that generates a QR code for the user to scan. When the user does this, both questions are answered.
- A Circle User ID and list of hashed emails for all of the emails that end user is sent to the Web server or application.
- The Web server or application then just checks for a match in a table it has created for this purpose.
- Circle Access Mobile then authenticates the end user and returns a Yes or No to the Web server or application.
You can learn more about how Circle Access works here:
Circle Access Mobile
Circle Access Mobile is a standalone authentication solution to log into any Web site or application.
- Your Smartphone is You.
- By scanning a QR code, the end user can log-in to any Web site or application on any device (mobile, desktop/laptop device, tablets, etc.)
These are the high level steps involved to implement Circle Access Mobile. For most situations, this can be completed in 30 - 60 minutes.
- Set up an account and get your license keys and App keys.
- Implement the integration steps on your Web site or application server.
- Authenticate your Web site or application server with the Circle Access server.
- Add the basic UI elements needed - such as log-in and log-out buttons, etc.
All of the other UX features and functionalities needed by an end user are provided by the Circle Access Mobile Application. This makes supporting Circle Access Mobile super easy: there is nothing to support for end users!
You can follow our step-by-step Getting Started guide here:
Circle Access Desktop
Circle Access Desktop is a standalone authentication solution for Desktops and Laptops only. It leverages the Circle Access cloud server via Circle Service, which is part of the Circle Access Desktop thin client.
- Your Device is Your Login.
- User must have Circle Access Desktop installed on the device that is logging in to the Web site or application directly.
Circle Access Desktop is currently only supported on Windows. MacOS users are given the option to use Circle Access Mobile as above. There is nothing the Web site or application owner or developer needs to do to enable this - it is automatically handled.
These are the high level steps involved to implement Circle Access Desktop. For most situations, this can be completed in 30 - 60 minutes.
- Set up an account and get your license keys and App keys.
- Implement the integration steps on your Web site or application server.
- Install Circle Access Desktop on any testing devices you wish to use.
- Authenticate your Web site or application server with the Circle Access server.
- Add the basic UI elements needed - such as log-in and log-out buttons, etc.
When an end user arrives at your Web site or application requesting authentication, Circle Access Desktop performs the authentication in exactly the same way as Circle Access Mobile - but with no mobile phone or QR code scan required because the private key needed for authentication is already on the device being used. Thus, Circle Access Desktop is a entirely frictionless UX. You can follow our step-by-step Getting Started guide here:
All of the other UX features and functionalities needed by an end user are provided by the Circle Access Desktop thin client (we call this 'Circle Tray'). This makes supporting Circle Access Desktop super easy: there is nothing to support for end users!
Remember: Circle Access Desktop is a desktop/laptop only solution. If you wish to support log-in for mobile devices, or the option for authentication by the Circle Access Mobile application, you should implement Circle Access 360.1
Circle Access Lite
Circle Access Lite doesn't require any form of end-point-device installation but it will use the browser functionalities to enable credential-free authentication.
It triggers authenticators on the browser to provide the biometric information of the user with device signatures and then the remaining part of backend credential-free authentication is similar to that of Circle Access Mobile and Desktop
These are the high level steps involved to implement Circle Access Lite . For most situations, this can be completed in 30 - 60 minutes.
- Set up an account and get your license keys and App keys.
- Implement the integration steps on your Web site or application server.
- Authenticate your Web site or application server with the Circle Access server.
- Add the basic UI elements needed - such as log-in and log-out buttons, etc.
When an end user arrives at your Web site or application requesting authentication, using Circle Access Lite a QR code will be displayed which the user will scan with any mobile device - this acts as a trigger to get the user details from the browser of the device which is trying to login. The details and device signatures are shared to Circle server and Client server where the credential-free authentication is carried out in a similar fashion as that of Circle Access Mobile or Desktop
Which solution is best for my application?
Generally speaking, we recommend Circle Access Mobile + Desktop as the best solution because of the flexibility it provides to your end users. Based on the feedback we have received; we have found the following advantages to these respective UX options.
Circle Access Mobile
This UX option is generally very important for any user that:
- Spends a lot of time away from their desk; and/or
- Needs to gain access to Web sites or application on other devices which they do not exclusively control.
Users that share workstations are an example in office settings - or in the home workplace now with laptops and desktops shared by family members. Users that travel frequently often need to gain access to resources in Internet Cafes, Airports and devices of owned and controlled by other people. Circle Access Mobile supports this kind of flexibility that is required in today's distributed, mobile work environment while preserving unrivaled security, visibility and control over who is accessing Enterprise resources.
Circle Access Desktop
Circle Access Desktop is generally preferred by users that:
- Work mostly or exclusively on laptop or desktop devices that they control; and
- Want to have a completely frictionless UX - enabling them to stay logged in and hop between different sites while maintaining rock solid.
Circle Access Desktop can also be used in situations where users share laptops, desktops or workstations by leveraging biometric scanning and other steps to ensure that the authorized end user is in fact on the device. However, in most situations like that, Circle Access Mobile will be both more secure and easier to use.
Circle Access Lite
Circle Access Lite is generally preferred by users which
- Just want the credential-free authentication and access the website or application though a browser.
Using Circle Data End-to-End Protection for Credential-Free Authentication
As noted above, this method of Creddential-free Authentication is implemented when the Identity and Access Management systems - whether that is the back-end of a Web site or application, or an integration partner of Circle such as Auth0, ForgeRock, Ping Identity and others. In this case, the role of Circle is restricted to protecting data used for authentication purposes in Secure Capsules that are controlled by the Web server / application or IAM platform.