Circle Data
End-to-End Data Protection

Safeguard your data on endpoint devices and Cloud
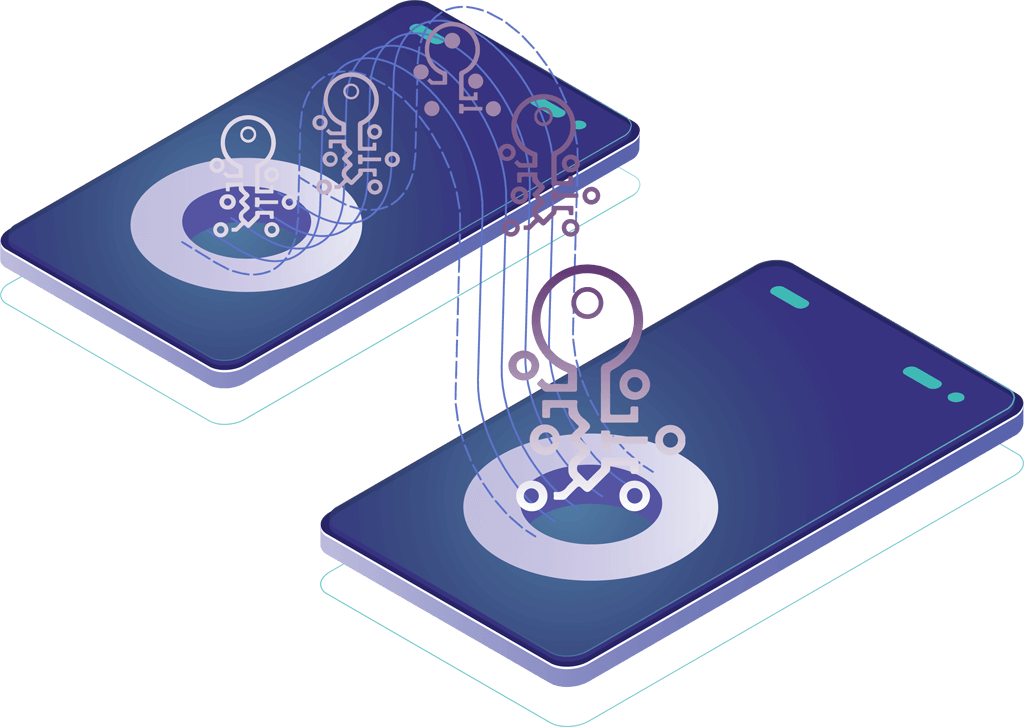
Circle Data puts data owners in control with AES encrypted Secure Capsules, created and controlled by endpoint devices
End-to-end data protection has a unique hybrid P2P + Cloud architecture that powers its capabilities for data security, privacy, and control.
Start securing nowFinally, E2EE that scales
Circle's unique patented key management ditches the constraints of PKI to power End-to-End Encryption in applications without compromising scalability.
Exchange and store unlimited volumes of data securely and persistently for collaboration and communication.
Multicast encrypted communications to groups of ANY size with no additional overhead on the transmitting device or transport servers.
Patented, out-of-band key exchange
Circle's unique patented peer-to-peer authentication eliminates the use of any central certificate authority, credentials, or cloud-based identity databases, with all operations conducted within an AES-256 encrypted Circle.
Maintaining cloud efficiency and flexibility without security headaches
Data encryption and generation of encryption keys are done on endpoint devices — and NEVER in the Cloud, eliminating the attack surface on the cloud. It's generally difficult for bad actors to attack endpoint devices as they are distributed across the board.
Large data files can be kept in the cloud while keys stay on the endpoint device. Pull and use on-demand just like any cloud application.
Data is not useable on unauthorized devices
Keys are bound to the endpoint device and cannot be taken off the authorized device or used anywhere else. Enterprise data can be made useable and accessible only on devices authorized to have the keys.
Frictionless UX at the highest level of security
With Circle, no compromise exists between a great user experience and unrivaled privacy and security.
Secure emails, attachments, documents, files - and containerized data - seamlessly, in the background, with no change to your user experience workflow.
Circle Data UX
invisible and integrated
- Install thin agent 1X
- Add and configure plug-in / other integration
- Just use your apps with built-in Circle Data protection
Demo: A secure way to encrypt an email
Most encrypted email systems claim to be secure since they leverage an external key store to hold the keys used to encrypt and decrypt the email. The problem is, when the message needs to be displayed, the ‘server’ needs to ask the external key store for the decryption key, which means that while the server doesn’t store the key locally, it can still get it.
Go to our demo page for a video recording of integration with Microsoft Outlook, along with code samples and explanations of how to implement it.