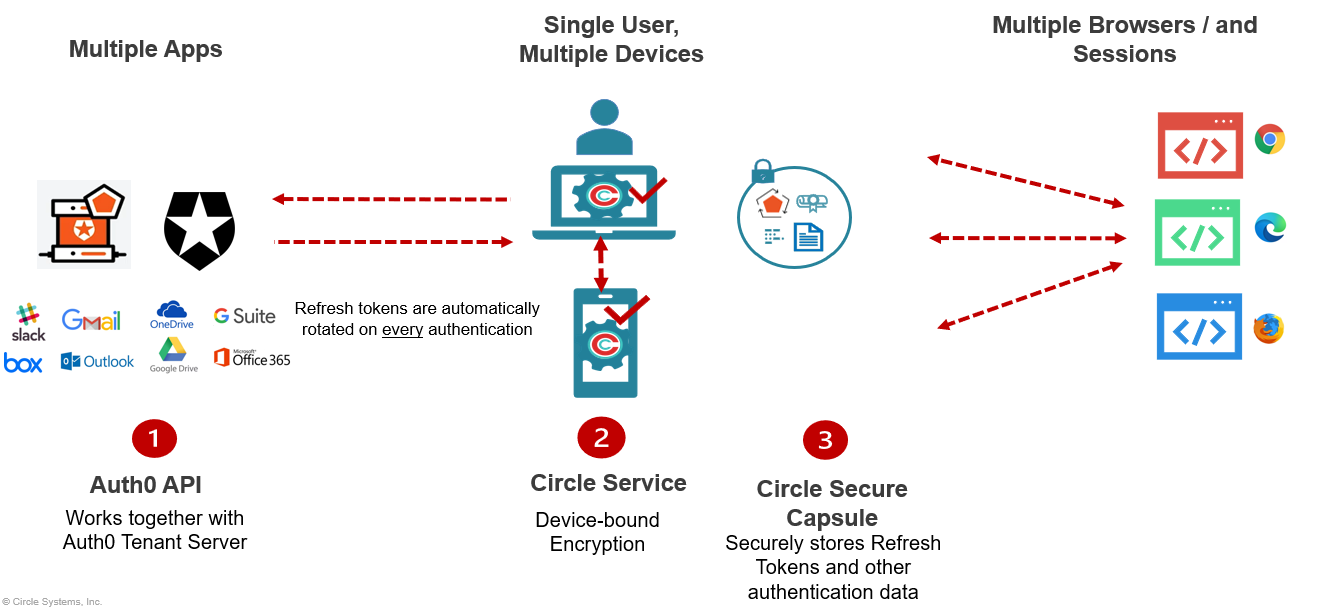
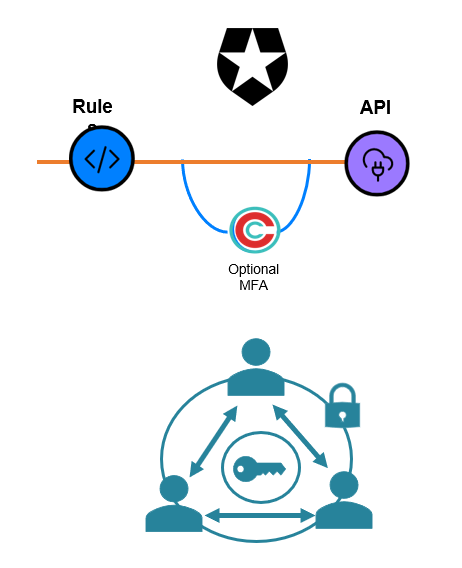
Continuous frictionless authentication of a single unique user across multiple devices, browsers, sessions and contexts without the need for a VPN, 3rd party cookies, usernames or passwords.
Circle delivers unrivaled credential-free authentication by combining:
- Something you have - A private AES 256 key cryptographically fused to an authorized device; and
- Something you are - Continuous biometric authentication tied to the device context