Downloads
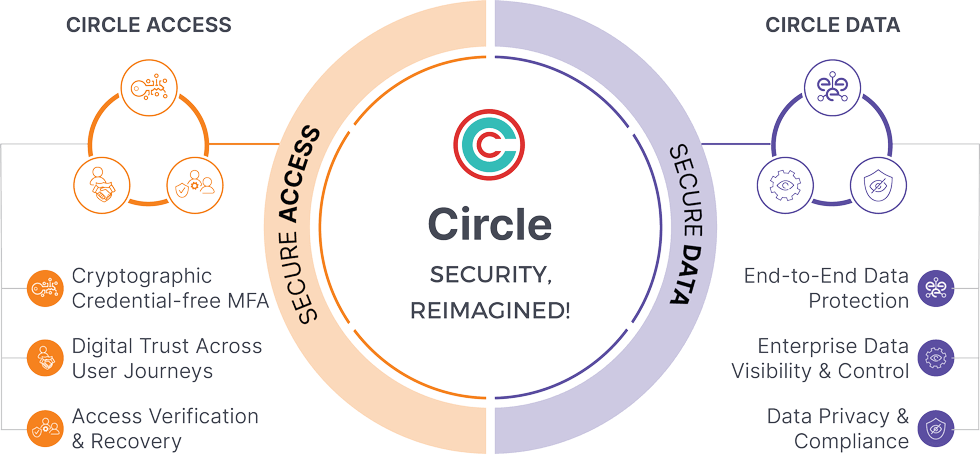
Circle Access secures access to data throughout the user journeys by eliminating all credential-based threat vectors using end-point cryptography and no usernames/passwords. Traditional MFA and Authenticator Apps are an improvement but are still vulnerable to various hacks with a single-point-of-failure
Easy to deploy
Easy to use
Easy to support
Circle Data uses the same endpoint-bound cryptography used in Circle Access, but Circle Data provides end-to-end protection for data assets and collaboration. Enterprises get seamless visibility and control into data on endpoints thus enforcing data loss prevention
Easy to deploy
Easy to use
Easy to support