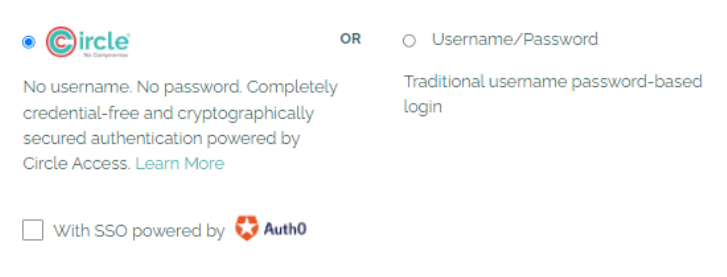
We implemented Circle Access Desktop to power credential-free authentication as an option for log-in for all customers.
While that is ultra-secure, there is still one step further that we can and will take soon: to replace the secret with the public key of a public/private key pair that can be used to cryptographically challenge and validate the device for each authentication.
The Auth0 Integration enables integration Circle Service to authenticate and communicate with Auth0. The developer can add any identity provider that is supported by Auth0. For this demo, we selected Google/Gmail and LinkedIn. Simply pick the one you prefer. The user is authenticated by Auth0 using the API and then the following process commences.
1.
The user requests and securely receives the Access Token and Refresh Token
2.
The Access Token is used to log the user in.
3.
The Refresh Token is securely stored in a Circle Secure Capsule on the device for future frictionless logins.
After this process, the user no longer needs to provide credentials, including passwords or any other information, to authenticate with the Identity Provider for all future sessions.
This is because the user has been identified by Auth0, which in turn has authenticated against Circle using the Refresh Token so that both parties are satisfied with each other’s identity prior to issuing an Access Token.
Logging Out
When the user logs out of the Developer Hub, the refresh token remains stored in Circle Secure Capsule. The user can then log in again using this stored token.

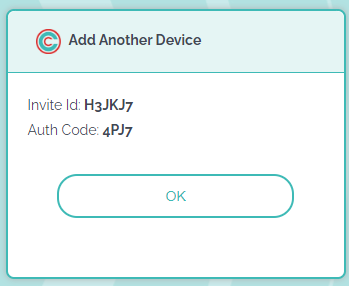
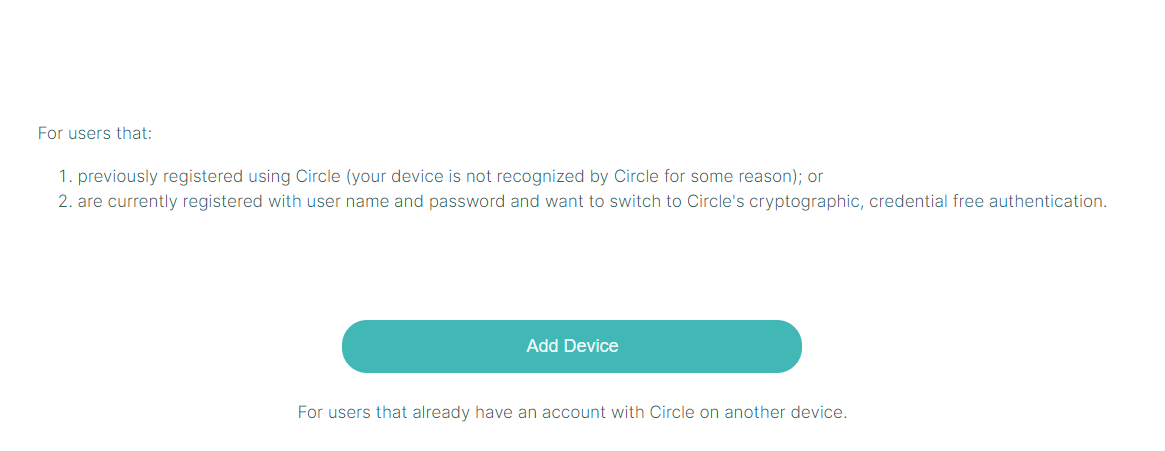
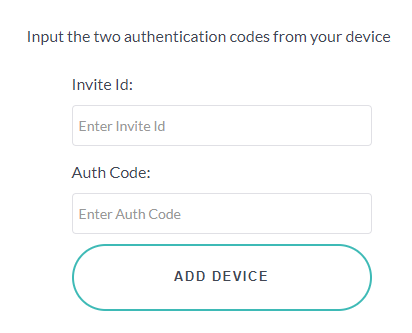
With Circle Access Desktop, you can also invite and authenticate any other devices that you own or wish to use. You do this via our patented, peer-to-peer out-of-band authentication process. When completed, the Circle - and any Secure Capsules it contains - will be synchronized automatically with your additiojnal devices at all times. Here is how to do it.
If the codes match, your new device will be authorized and the Circle on your inviting device and any Secure Capsules it contains will be synchronized to the new device. Now you can enjoy credential-free secure authentication on that device just as if it was the original.
Circle also enables users to be authenticated and log-in to any Web site or application across any browser - without the need for any additional steps. This is because the Secure Capsule stores whatever is needed to authenticate securely on the endpoint device. Unlike a cookie, Secure Capsules are:
- Totally secure (AES 256 encrypted);
- Accessible ONLY by your Web server or application; and
- Can contain an unlimited amount of data that cannot be messed with by the user or any attacker that gets onto that device.