Downloads
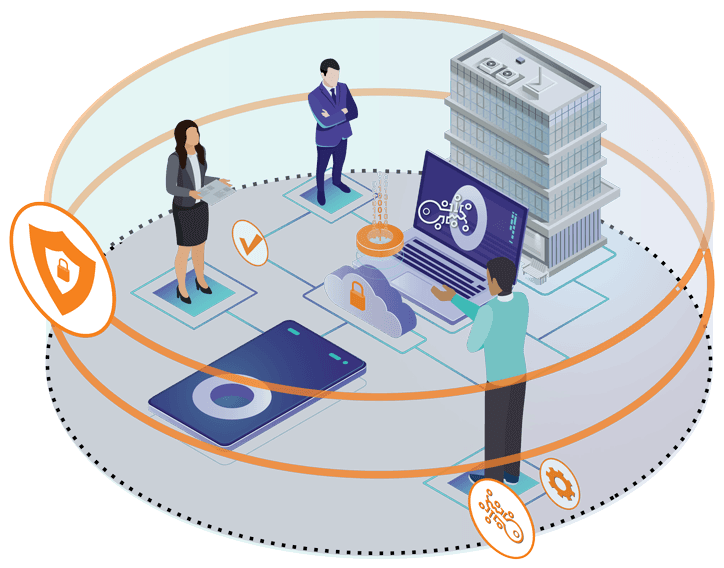

Our human-in-the-loop step-up authentication is executed using decentralized cryptographic multi-factor authentication.


To ensure a smooth recovery process there should be a specific set of users with super accesses. In other words, superpowers are required for users who can override when needed to recover and protect the system. With Circle, these super users will be reinforced by people who know each other personally and beyond machines.

Faster deployment, i.e., within minutes
No more unnecessary login friction!
No VPN, firewalls, or SDP is needed.