Recover your access to private data
easily and in a trusted way
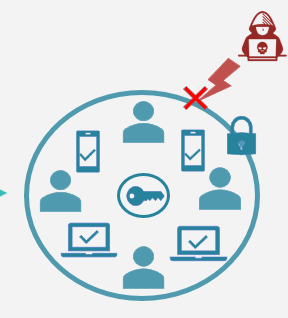
Ironclad security usually has a dark side. If the credentials, passphrase, and hardware token are lost, access to critical and valuable digital assets and data can be lost forever.
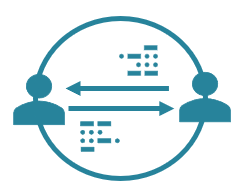
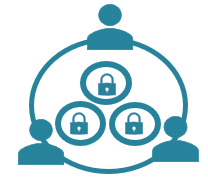
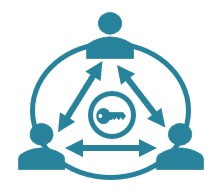
Circle-of-Trust enables users to set up private networks of trusted persons they know who can authorize and restore access to encryption keys but never use them directly.
With Circle, users can have Peace of Mind knowing that access to their digital is entirely secure but always recoverable.