The architecture and approach of Circle Access differs from a certificates in several significant ways. There are two common use cases for X.509 certificates:
We will focus here on securing email.
The exact same certificate can (and, unless extreme measures are used) MUST be used on every device used to generate or read email for that email address. Therefore, unless secondary measures are used (such as a password on the certificate), the possession of the certificate alone is sufficient to become that email address. Virtually all X.509 certs are password protected for this reason, which means that the use must re-type the password, or the password must be stored in a local keystore.
X.509 certificates can’t be used before or after the set validity time to prove identity. While a developer can set an expiration time for Circle, there is no requirement to do so.
If that process is weak or compromised, then the security of every session for all users is broken. Circle, on the other hand, requires each user to perform an external authorization to that is distributed and delegated to each user to ensure their identity. There is no certificate that can be compromised or hijacked. Circle further can enforce an external very strong identity verification: a biometric scan of the user - which can be enforced on every authentication, or even continuosly. Circle also offers step up escalation to human-in-the-loop identity verification whenever desired.
While most vendors that use X.509 certificates demand proof of ownership of an email address, there are many ways that this can be spoofed. Here are just a couple of examples.
With Circle Access, on the other hand, three very strong factors are used to authenticate:
X.509 cetificates can and often are archived on generation in order to ensure that messages encrypted with a given certificate can be accessed later (if the passwords are also archived). For certain compliance environments, this can become critical. Unfortunately, this is also a very attractive target for an attacker, since breaching this can then open ALL emails.
Circle also can archive and preserve all the contents of all Circles and Secure Capsules containing encrypted emails. In fact, this is done automatically with Circle's store-and-forward Web services and cloud server. This server, however, has NO keys - and of course no passwords since there are no credentials in the system at all. So once again, there is no central repository that an attacker can go after. Instead, the attacker must breach the individual devices which possess the keys to the Circle and Secure Capsules they were members of. This exponentially increases the cost and effort.
If a company wants to maintain a central repository of keys - for compliance reasons - it can do so within a Circle-of-Trust. This can enforce a distributed, out-of-band human-in-the-loop identity verification between users that know each other in order to release keys to open designated Circles. Again, no central authority, nothing to attack in the cloud. Even compromising a device does not help - only 'breaching' or corrupting or coercing one of the human participants will suffice. Circle's internal immutable ledger ensures, however, that in the event of even the most extreme form of attack there is an audit trail of all events and actions that occured.
X.509 is supported by every significant email client, and many web-based email clients and all mail transports support it.
Circle is not explicitly 'supported' by email clients because it does not have to be. The payload of each message and any attachments is encrypted, not the headers. So any email client and email transport system can send and deliver emails secured by Circle with no issue after a simple integration is performed.
Yes. "MFA Bombing" is a new type of exploit that defeats traditional MFA that many organizations believe to be quite strong. This recent article in Ars Technica provides a good summary.
As Ars Technica points out, any MFA is better than no MFA. But there are important differences between different types of MFA, and common vulnerabilities to those in the widest use today.
Circle Access, on the other hand, uses 3 very strong factors that are immune to cloud-based attacks of all kinds - phishing, pharming, spoofing, MFA prompt bombing, etc.
With Circle, authentication is device specific. The only opportunity is for a hacker to get onto the device.
Circle leverages the OS-native biometric scanning capabilities the device to ensure that the authorized user is in fact using the device.
With traditional MFA, this is weak and spoofable - using channels like SMS and email and authentication codes. Circle Access has you do something which uniquely proves your authenticity: sign a cryptographic challenge.
The only way to break this once again is get possession of the device. Then, for the highest value use cases, Circle adds one entirely new method of authentication.
Circle-of-Trust human-in-the-loop identity verification. Even if the device is physically stolen or remotely hacked, escalation to Circle-of-Trust can force the attacker to 'lift the veil' and be identified directly, in person. This happens completely out-of-band and directly between the parties - no CoT bombing possible.
And of course the other vital role for Circle-of-Trust: protecting your super-powers!
Even when companies use FIDO2-based MFA everywhere, Nobelium has been able to defeat the protection. That bypass, however, was possible only after the hackers completely compromised a target's Active Directory, the heavily fortified database tool that network admins use to create, delete, or modify user accounts and assign them privileges to access authorized resources. That bypass is beyond the scope of this post because once an AD is hacked, it's pretty much game over.
Ars Technica: Lapsus$ and SolarWinds hackers both use the same old trick to bypass MFA
How Circle Access Mobile and Circle-of-Trust works, including API details, related forum topics, and relevant FAQs for developers
"Blockchain" and "Distributed Ledger Technology" (or "DLT") are too very big buzzwords today that are often misunderstood, or misused. Here is where Circle fits.
Blockchain is a decentralized, distributed and often public database type where data is saved in blocks, such that the hashcode present in any block is created using the data of the previous block. These blocks offer a complete set of characteristics like transparency, immutability, and scalability
Blockchain vs DLT – An Explanatory Guide
Blockchain has many compelling applications and use cases, but most of these revolve around some form of enables parties that do not trust each other to verify any transaction without involving any intermediaries.
This is a definition according to the framework of the 'Crypto' world.
DLT is a digital system used for storing the transaction of assets, even when the data is stored at multiple places simultaneously. It might sound like a traditional database, but is different because of the fact that there is no centralized storage place or administration functionality. Meaning, every node of the ledger processes and validates every item, and this way, contributes to generating a record of each item and building a consensus on each item’s veracity.
Blockchain vs DLT – An Explanatory Guide
Some of the advantages of DLT are considered to be the following.
The most important thing to understand is that Blockchain is a form of DLT - one type, a sub-set. DLT is the broader concept.
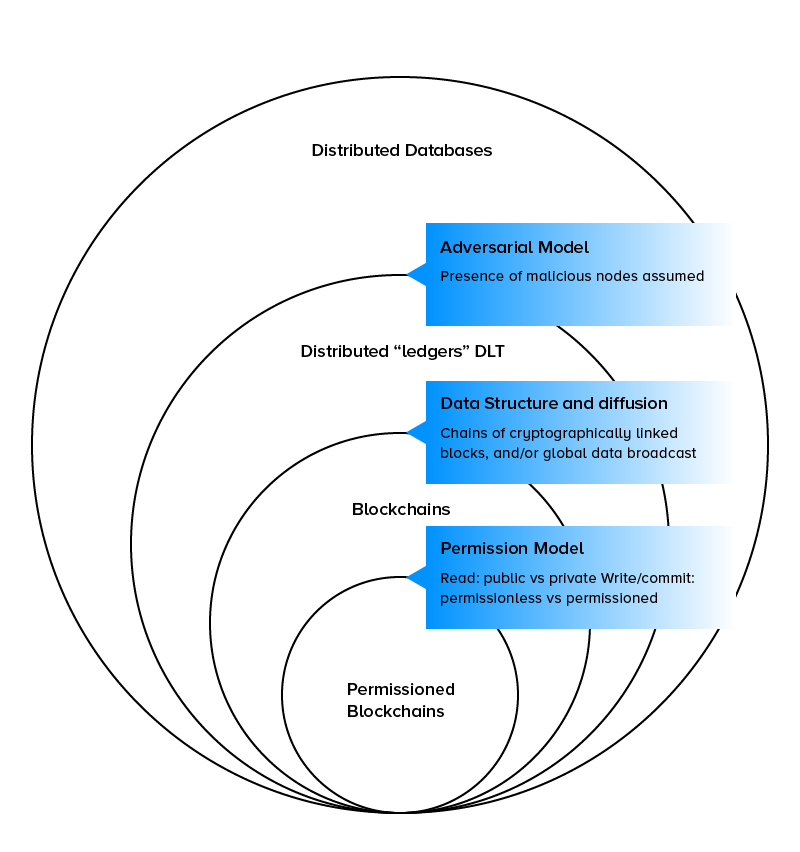
Circle's internal, immutable DLT meets - and exceeds - all of these advantages, and was architected for similar objectives.
The way it works in Circle is that each device generates a ledger - and append only file - of its actions. That's all it can do. Every device gets a copy of all the other devices files, and the complete ledger of all the actions between that group of devices is assembled in "run time". When the user is viewing/working. If there is an "edit" or "deletion" of something, an entry is made in the ledger on the device that does it. Then when displaying the edit or deletion is applied, but the original entry is unchanged. No device can change the entries of another, and if any change was made nefariously it can be detected.
In the wider world of DLT, the presence of 'adversarial nodes' is a potential issue because the ledger is spread out across thousand or millions of users and all kind of servers owned by different parties participating in a shared ledger. With Circle that is not an issue because the DLT is internal to an AES 256 encrypted "Circle" between a small number of users.
Most people don't differentiate, and of course Blockchain is the sexy term to use. But there are several differences that are critical to the kinds of use cases that Circle is focused on solving.
When your want to have a digital currency, for example, this overhead that comes with Blockchain is worthwhile. But when you just want to have immutable, auditable data trails that can be trusted, it's preposterous.
Circle has an internal immutable DLT, not Blockchain. We have all the benefits of Blockchain - Immutable, Encrypted, Private but Trusted, Verifiable, Auditable - with none of the overhead.
When we have use cases that require blockchain, than Circle will integrate with it. Especially Calendar Hashchain, which has a proof of participation architecture that is orders of magnitude faster & planetary Internet scalable. The "Block" of blockchain - the protected data of the whole transaction or whatever it is - in our case is inside of Circles. But with speed and scalability.
But that's the topic for another day!
Circle Access 360 integrates:
The technical details of this are beyond the scope of this article, but we will try to summarize briefly here.
With CAM, your smartphone is you. It accomplishes this by securing two very strong factors:
CAD leverage cryptography to create something even more interesting: a Circle Secure Digital Capsule. These have several very powerful characteristics.
So, with CAD, the device on which a Secure Capsule is installed and authenticated to be controlled by YOU is your log-in. No credentials, zero friction.
Secure Capsules are themselves then bound to the device cryptographically - each capsule can only be opened and used on the specific device it was authenticated upon.
Secure Capsules can also be used to store biometric data. When you do this, then the capsules are bound to YOU independent of the device. That has many useful and powerful applications.
With Circle Access 360, an authentication process is conducted that enables your smartphone (with Circle Access Mobile) to securely communicate and control the secure capsules on your devices created by Circle Access Desktop. This delivers many important benefits:
This integrated capability then powers many other powerful capabilities across our product line. The bottom line is that 1 + 1 here equals far more than 2!
How Circle Access Mobile, Circle Access Desktop, and Circle Access 360 works, including API details, related forum topics, and relevant FAQs for developers
The benefits of using Circle Access Desktop include:
With Circle Access Desktop, your device - PC, laptop, etc. - is you. As long as you are on that device, you can be authenticated and log-in completely friction free.
Circle Access Desktop works by leveraging cryptography to create something very powerful and useful: a Circle Secure Digital Capsule on each device that has been authenticated and authorized. Anything can be stored in secure capsules, but in the case of credential free authentication, we store.
As a result, CAD secures two very strong factors:
1. Something You Have
The PC, laptop or other device you work on every day. CAM leverages cryptography to bind a unique private key to your device, which only your device can have.
Devices can be stolen, or family members or work colleagues can get on to them when you are away of course. So CAD support multiple ways to ensure that only the authorized user is logging in.
2. Something You Know
PIN codes and other secrets are a common method. They can be kept in your wallet, or in your brain.
3. Something You Are
Biometrics can be used as proof of you. Most new PCs and laptops have this these days, of course - or it is readily accessible accessory & upgrade. With Circle Access 360, the biometric scanning and continuous authentication of Circle Access Mobile can be leveraged to verify the identity of the user logging in on the Circle Access Desktop. CAM can also be alerted every time there is an attempt to log-in by CAD.
The result of this is to provide completely frictionless cryptographic credential-free authentication that binds user access to authorized, registered devices. Unparalleled security with unrivaled User Experience. No Compromise.
There are many benefits to using circle-of-trust, including:
Enable direct identity verification of a user, via other trusted and known users who are cryptographically added to the Circle-of-Trust. Developers can easily integrate the API calls to Circle-of-Trust into their workflows in minutes.
Authorized members of a Circle-of-Trust operate entirely as an encrypted user group, without any external avenues for attack.
With the available API hooks and guidance, enterprises can implement their own variations of Circle-of-Trust, while ensuring the security and integrity of the system is maintained.
Anyone who has ever used a password manager, crypto wallets, etc. has also read all the horror stories. What happens if you LOSE the critical hardware token, passphrase or other recovery mechanism? You are locked out, and there is no recovery.
With Circle-of-Trust, any verified member can restore access and recover the Circle-of-Trust owner, without any possibility of gaining access to the owner's secrets themselves.
The Circle-of-Trust owner invites and verifies members that have the power to restore his/her encryptions keys and access.
The number of members for identity verification to authorize recovery, can be set by the Circle-of-Trust owner.
We all read the headlines. Not a day goes by without another catastrophic breach of data, networks or sensitive systems and infrastructure. Why does this keep happening? Partly because the super user or the privileged access user has the keys to the kingdom. And those keys are usually stored in the place where they are most vulnerable – on the cloud!
Circle-of-Trust solves this problem, enabling Super User access to be reinforced by humans that know each other beyond machines.
Worried about users that do silly things? Application developers can easily offer a cloud back-up that is automatically created when users create a Circle-of-Trust.
Recovery keys are stored on the cloud, but in secure capsules that can only be opened when downloaded to an authorized device of an authenticated user. So, your support staff can recover a user, but never get access themselves.
Circle's internal immutable Distributed Ledger, ensures that a bullet-proof audit trail can be maintained for compliance and regulatory investigations.
Circle-of-trust is a zero trust identity verification system that uses contextual information to verify the identity of a user. This system is unspoofable, meaning that it cannot be fooled by fake or stolen credentials. It also does not require any external certificate authority, making it more secure than other systems. All operations are performed within encrypted cycles, ensuring that your data is safe from prying eyes.
Not all security needs or use cases are equal. Circle Cryptographic Credential-free Auto-Authentication is suitable to many or even most use cases, providing a new level of security that binds access to cloud resources to authorized devices. In doing so, we have eliminated the attack surface in the cloud.
Attackers may then turn, of course, to attack devices. While this is exponentially more expensive in terms of effort required for the attacker, it will still be worthwhile if the human or device involved accesses sufficiently valuable resources. A Master Admin account is one example of this, but any use case with high value and high risk capabilities applies.
Circle-of-Trust provides a breakthrough method of addressing this need for such capabilities, while ensuring that only the authorized human users or roles are given the power to do so.
There are many benefits that users can enjoy with Circle Access, including:
Circle replaces insecure passwords with private keys, created and stored in secure capsules that are bound to each device, and cryptographically validated during each login. Supports a single user across devices, browsers and contexts.
Optionally, leverage the built-in device biometrics to verify the identity of the user at the time of authentication.
Cryptographically bind authentication to the specific user and device that has been authorized.
by allowing them to switch browsers and devices without the need to re-authenticate, all without compromising security or privacy
Circle secure capsules can cryptographically store the user biometric data and provide immutable proof of the identity of the user in possession of the device independent of the operating system.
of device security posture and other metadata at the exact time of authentication for every user and every device requesting access.
There are many benefits that businesses can enjoy when they make use of Circle Vault. Some of these benefits include:
-Unrivaled Visibility and Control: With Circle Vault, businesses have complete visibility and control over their enterprise data. This means that businesses can easily manage access to their data and ensure that it remains safe and secure at all times.
-Guaranteed Cloud Backup and Restoration: Even without the use of keys, businesses can rest assured that their data will be backed up and restored in the event of a disaster.
-Offboard Employees and Vendors Quickly and Securely: When the need arises, businesses can easily offboard employees and vendors without having to worry about the security of their data.
-Completely Seals Off Enterprise Data from Unauthorized Devices: Circle Vault provides businesses with an added layer of security by completely sealing off enterprise data from unauthorized devices. This ensures that only authorized devices have access to your data, keeping it safe and secure at all times.