Cryptographic Human-in-the-Loop Authentication
Circle-of-Trust enables direct authentication between human users, implemented by the developer using traditional cloud resources for re-authentication and checks to ensure that the authorized user has control of their devices.
Developers can implement this end-to-end themselves with existing preferred cloud resources and services, or Circle offers optional hosted services. If you want to dive straight into the code, please see:
How It Works
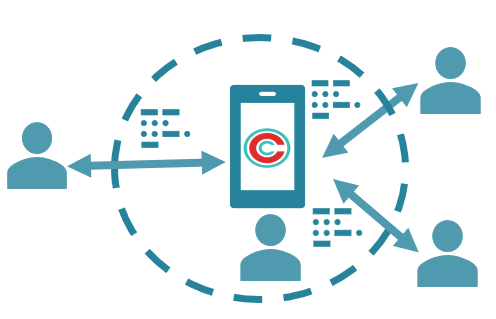
With Circle-of-Trust, a special kind of Circle is created, whose purpose is dedicated to enabling users to verify and authenticate each other through a direct human-to-human process. When users form a Circle-of-Trust, other members do not have access to any Secure Capsules or Circles controlled by the Owner of the Circle-of-Trust. They only have the ability to verify the identity of another user in the Circle-of-Trust that is trying to perform a restricted action.
The policies that govern restricted actions and the details of what steps are required in an authentication operation are up to the developer. Circle API provides the mechanisms and hooks to implement. The two key capabilities involved are mechanisms for
- Locking
- Unlocking
Locking the Capsule
This uses the same Circle cryptographic authentication process, but incorporates human-in-the-loop verification that is orchestrated by an IAM platform or Application Server. Developers can use their own preferred communications platforms for messaging, or use the turn-key service option provide by Circle.
The trigger & lock process is the same
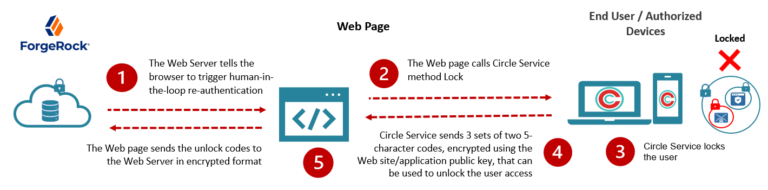
But the re-authentication process can be configured & customized
Another capsule contains the rules to unlock the user. These can be as elaborate or as simple as the developer or customer admin defines. In this case, we’ll use an example of re-authentication requiring 3 humans to verify the identity of the user.
Unlocking the Capsule
In this use case example, 3 people that know the user and can verify his/her identity are required to re-authenticate. Authenticators are people that know the user. They may but do not have to be Circle Service users.

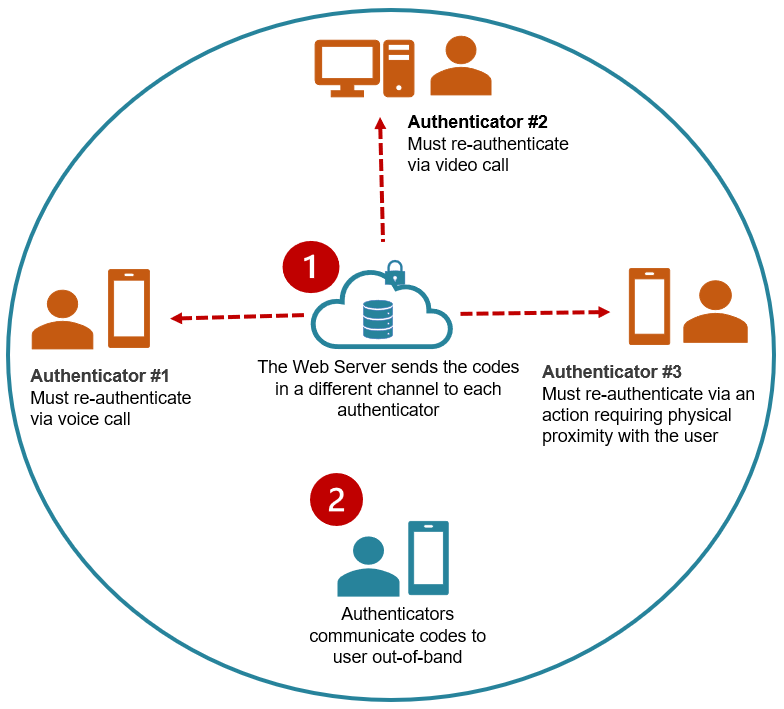
Identity Verification + Authentication
Depending on the degree of security desired, authenticators can communicate their codes to the user via two separate channels or completely out-of-band. Additional steps and checks, such as verification of proximity, biometrics or other can be applied.
Unlock (Authorize)
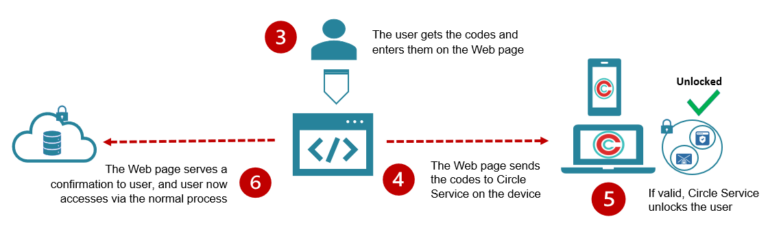
When the user inputs the codes received into the Web page, this validates the identity verification performed by other human users. The policies governing what steps are required for identity verification can be set and stored within the Circle Capsule, or defined and governed in 3rd party IAM platform or otherwise.
