Overview
Circle's credential-free authentication replaces password-based log-ins with a cryptographic method of storing secrets - or at the highest level, cryptographic signatures - that uniquely restrict and bind authentication to log-in to any cloud resource to the specific user and device that has been authorized.
There are two ways that you can do to this with Circle.
1. Circle Access Cryptographic Credential-free Authentication
This is a turn-key solution that can be implemented by any developer or Enterprise with no code or low code in 30 to 60 minutes.
2. Implement Credential-free Authentication with Circle End-to-End Data Protection
It is also possible to implement credential-free authentication by integrating Circle REST API and leveraging Secure Capsules together with the back end of a web site or application or any Identity and Access Management systems. In this case, the role of Circle is restricted to protecting data used for authentication purposes in Secure Capsules that are controlled by the Web / application server or IAM platform.
This enables rapid, easy but secure user self-authentication and can be integrated with IAM, ADFS and any token-based authentication platforms. Highlights include:
- Zero trust authentication that is cryptographically fused to your device and requires no passwords, usernames or any credentials.
- Eliminate phishing and any other threats from stolen or lost credentials.
- Works across browsers, devices and contexts.
Out-of-the-Box Integrations
We have two out-of-the-box integrations and implementations of this approach available now:
and more coming soon! If you are a customer or partner of these companies, you can deploy this integration in a matter of hours.
Custom Integrations
You can also do your own integration and implementation of Circle REST API for credential-free authentication - and any other use cases leveraging the unique data protection, control and privacy capabilities of Circle Secure Capsules. This approach requires development expertise, resources and the functional capabilities of such systems. There are many benefits and capabilities of Circle Secure Capsules that go far beyond storing authentication data and can be leveraged in this implementation approach. If you are interested in this, we suggest that you contact us for a free consultation before starting.
Delegated Distributed Multi-Factor Human-in-the-Loop Authentication
When needed for high risk use cases, contexts and user profiles, Circle API proves flexible options to escalate to unspoofable distributed, peer-to-peer multi-factor identity verification + authentication. To learn more, please see:
End User Experience
Once you have integrated, end users just install Circle Service to enjoy credential-free authentication.
Users Install Circle Service
- Lightweight ultra-thin client.
- Browser plug-in UX.
- Install 1x and forget.
Users Authenticate
- DONE!
- No more passwords or credentials!
- Your device is your log-in, with user identity cryptographically bound to it.

Set Up a Circle-of-Trust
For Users and Customers that want advanced distributed unspoofable multi-factor human-in-the-loop™ identity verification + authentication.
How it works
Here is how we enable continuous authentication, with unprecedented security and ease of use cross-browsers and contexts, with refresh tokens stored inside Circle’s Secure Capsules - and any 3rd party authentication or IAM platform.
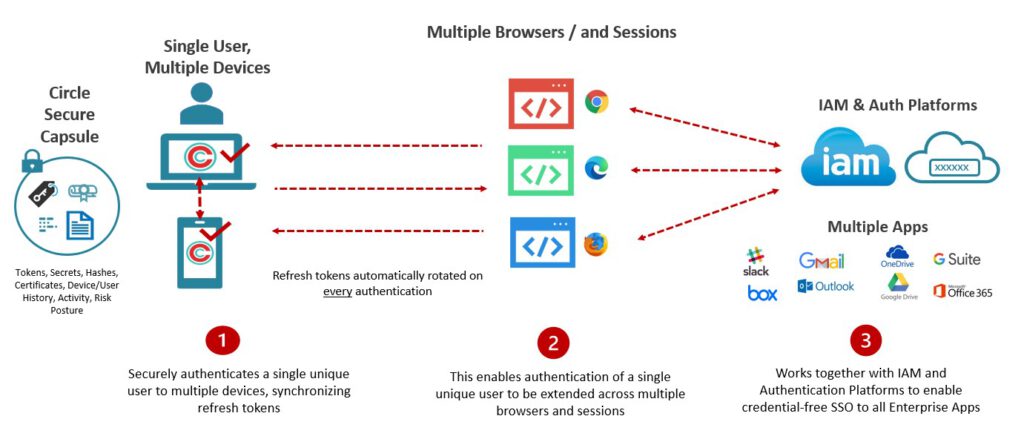
In this use case:
- The Circle is created with only one member - the End User.
- The End User can add and manage his or her own devices into the Circle.
- The application controls and has unique access to and control of the data in the Circle.
To see Cryptographic Auto-Authentication in action, go to:
Considerations
There are many different ways that credential-free authentication can be implemented with Circle Guard to address different levels of security in the design. The simplest design stores user credentials securely on the device. At the highest level, passwords can be eliminated entirely and replaced with cryptographic signatures that are uniquely bound to the device that is authorized.
We recommend that developers consider these guidelines and do not hesitate to contact us for a consultation.
What to store in Circle Secure Capsules
Ultra Secure - Recommended
- The private key of a public + private key pair can be protected in Secure Capsules and bound to each device that has been authorized.
- You can then store the public key on the Web / IAM server in order to perform cryptographic validation of challenges.
Note - we strongly recommend that you eliminate user passwords entirely, and only allow access via your integration and authentication with Circle Guard. Or you can benefit from our turn key solution with Circle Access.
Extremely Secure
- Long lived JWT generated by the App Server/Web site
- Signed hash generated by the App Server/Web site
Very Secure
- Password & other user identity information kept in its user database.
Example: ForgeRock Integration
Our partnership and integration with ForgeRock is a great example of how Circle can complement and enhance the capabilities of an IAM platform. Our initial focus and available 'out-of-the-box' are:
- Credential-free Authentication (as outlined here); and
- Circle-of-Trust Level 1
ForgeRock customers can also get a custom deployment of Circle-of-Trust Level 2 upon request.
Circle API can also be leveraged to deliver other important complementary innovations and advances in the areas of data security, control and privacy. The key to this is that the logical construct and components Circles and Secure Capsules, are extremely flexible and powerful. Once they are created and a user - or device - has completed identity verification, authentication and authorization - a totally secure and private environment has been established for all ongoing communications, data exchange and collaboration.
The diagram below provides a high level conceptual summary of the possibilities.
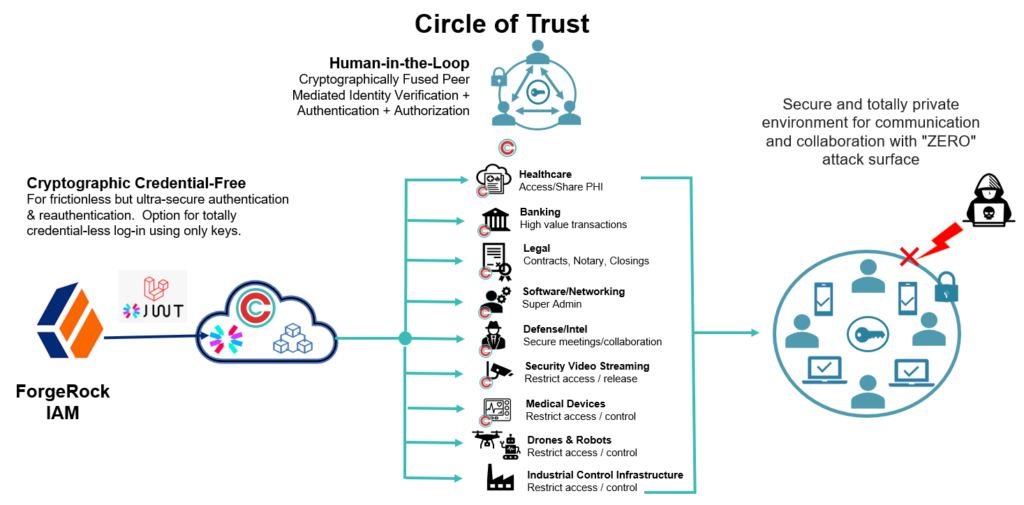
Use ForgeRock? Here's how you can add and integrate Circle API right now!
Example: Auth0 Integration
Our out-of-the-box integration with Auth0 show how Circle Cryptographic Auto-Authentication - and Circle-of-Trust Level 1- can complement and enhance authentication platforms. Developers can set this up rapidly and easily, leveraging these capabilities together to maximize both ease of use, privacy and security for their end users.
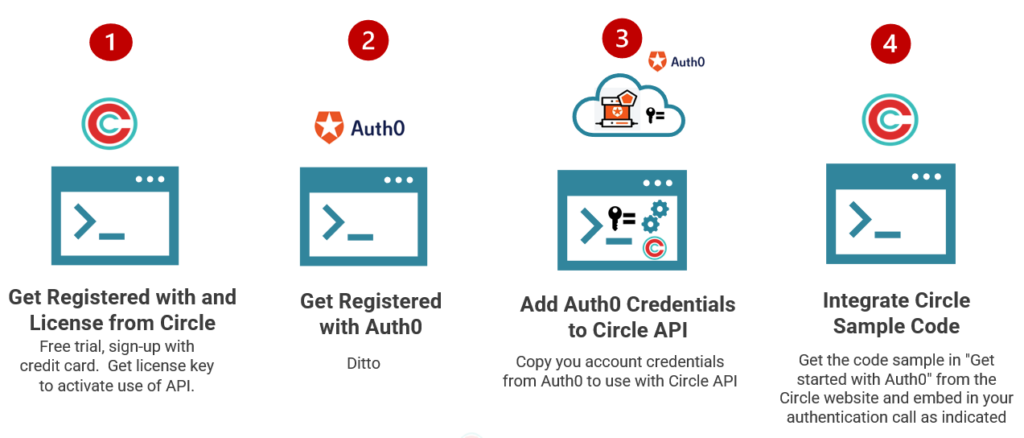
Want to use Circle API with Auth0? Here's how you can get started right now!



