Introduction
Circle Access powers a radically more secure - and private - method of authentication that eliminates all of the current major vectors of attack. If you have arrived here, then you probably already know that credential-based authentication - i.e. username and password - is a disaster waiting to happen to you and your users.
What you may not know is that the the new wave of passwordless authentication solutions + MFA - while an an improvement - are still vulnerable to cloud-based attacks. One-time codes and push notifications can be hacked at scale. Further, the inconvenience and friction these create for end users makes adoption slow and adherance spotty.
Passwordless Authentication + Traditional MFA is Not Enough
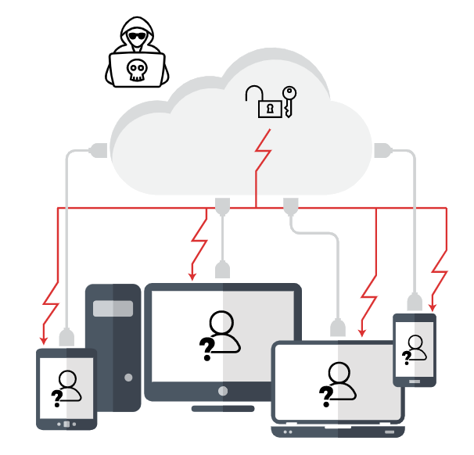
User PII and credentials are still stored in the Cloud. Even if hashed, any sophisticated hacker can crack them after gaining access.
Users are assumed, not known.
If an attacker gets the credentials or spoofs the MFA – which is trivial to execute – he or she can be anyone, anywhere/
Circle Access Changes the Game
Circle Access cryptographic credential-free authentication delivers unrivaled security with frictionless UX that your users will love – and use
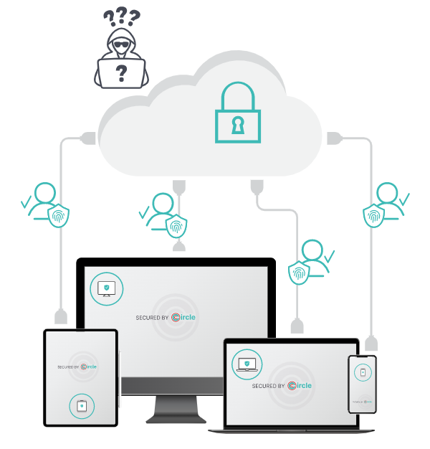
ZERO attack surface in the cloud:
- No private keys
- No credentials
- No user PII
- No central certificate authority
Users are bound to devices and biometrically verified.
Keys for secure capsules are bound to device keychain or TPM.
As desired, Secure Capsules can protect and manage additional authentication data that is accessible only to the Web server or application.
- Example: user activity and device risk posture
For the highest level of security, the private key for cryptographic verification of challenges can be stored in Secure Capsules and protected and controlled by Circle-of-Trust Level 2.
How does this work?
With Circle Access, there are no credentials - such as a user name and password, or any other method of creating and storing 'secrets' on a server that is used to authenticate a user. All such methods are deeply vulnerable to attacks.
Circle Access eliminates the attack surface in the Cloud with a method that restricts all access to authenticated devices, which are bound to authorized human users.
- A unique public-private key pair is created by the endpoint device.
- The public key is securely transmitted and stored in the Circle Access cloud server.
- The Circle Access cloud server has no credentials or PII (Personally Identifiable Information).
- It stores only a user ID and the public key.
- The end user can add and authorize additional devices directly, after which each device will now have a copy of that same private key.
- The developer, admins or end users can optionally use or require the use of device-based biometric scanning to ensure that the authorized user of the device is in fact the current user on the device.
- The private key is securely stored in the device keychain or crypto wallet, with the option of TPM on supported devices.
- For use cases requiring the highest level of security, the private key for cryptographic signature verification can be stored inside a Circle Secure capsule, where it can be protected by and subject to a Circle-of-Trust Level 2 human-in-the-loop identity verification and cryptographic authorization.
- When a user wishes to log-in, Circle Access cloud server sends a cryptographic challenge using its public key to be signed by the private key on the device.
- When the signed challenge is returned by the endpoint device, the Circle Access Server validate it - and if successful - approves access.
What makes this so secure?
This approach achieves authentication with 3 very strong factors:
- Something You Have. A smartphone, PC or laptop.
- Something You Are. Biometric verification, with the option to escalate to Human-in-the-loop Identity Verification with Circle-of-Trust.
- Something You Do. Validation of a cryptographic authentication that can only be done with the private key uniquely created on and bound to the endpoint device controlled by that human end user.
These ultra-strong factors eliminate all the current major vectors of attack. There are are:
- No credentials;
- No central certificate authority;
- No centralized database containing user PII.
There is simply nothing in the Cloud - either on Cloud servers or in transmission - which can be attacked, spoofed, stolen or otherwise misused by bad actors.
How can Circle Access not know users?
While the Circle Access server does have a user concept, it only knows a User ID. All PII - including emails and phone numbers - are encrypted by the private key of the endpoint device. There is no information on users that Circle Systems - or an outside or inside attacker - can gain access to on the Cloud Server. Only the end user, on the endpoint devices he or she has authorized, can interact with the Circle Access Server to store and use this information.
The Web server or IAM server of your Web or native applications store the Circle User ID, along a hash of any emails that the end user has authenticated. When the Web server wants to authenticate a device / end user that is requesting access, it securely calls the Circle Access server with the these two pieces of information unique to the user. Circle Access server than performs the authentication directly with the endpoint device and returns the result to the Web server or IAM server.
What if the user's device gets hacked/compromised?
So, with Circle Access, the only possible avenue of attack is through the endpoint device of a specific endpoint user. This dramatically increases the cost and effort for an attacker, while simultaneously radically reducing the blast radius. Attackers will have to compromise not only one device but all the devices, and if successful can only access what that device / end user can access.
Of course, some end users - and thus their devices - are particularly valuable and will still be targets of attack. To counter this, Circle Access adds two additional very strong defenses.
Biometrics
As noted previously, the developer, admins or end users can optionally require the use of device-based biometric scanning to ensure that the authorized user of the device is in fact the current user on the device. This is configurable based on the level of security desired. At the highest level of implementation, the scan used for biometric verification at the time of initial authentication can also be stored securely by Circle Service in a Secure Capsule which only your Web server or IAM server can access. This can be compared to the scan currently being used to ensure it has not been changed by an attacker that has gained control or a device.
Circle-of-Trust
Circle-of-Trust provides a step-up, human-in-the-loop method of verification of the identity of the current user on an endpoint device which - at the highest level of configuration - is completely independent of the device. The current end user must 'lift the veil' and show him or herself either in person or on a direct, peer-to-peer encrypted video conference - to other human users that know him. These human users than grant authentication - after verifying identity - with a direct, out-of-band peer-to-peer authentication method. This means that even control of the endpoint device by an attacker is not sufficient to defeat it. This method is once again highly flexible and configurable to adapt to the level of security required by a specific context, user risk profile or use case.